Enterprise Cyber Risk Management
Equifax points out—again—the need for speed in security management
The Equifax data breach illustrates again the need for speed in security management. If the breach was through a known vulnerability, we wonder why wasn’t it patched? If through another path, we wonder why wasn’t the attack detected? We have so many incident and event management tools for servers, desktops and networks, it is hard…
Read MoreAnatomy of a Security Breach
In recent Information Security news, The Wall Street Journal reported on the upcoming trial of an alleged botnet master. The trial is in progress now. It is not often that we get a look at the details of a computer security breach, but in this case at least some details are in the docket of the Eastern District of…
Read MoreThe Smartest Information Security Companies
Every year, MIT Technology Review publishes its list of the 50 smartest companies. This year, two information security companies made the list, along with big-time players like Amazon, SpaceX, etc. TR doesn’t publish detailed selection criteria, but they include things like ability to dominate the chosen market and innovative use of technology. The two security…
Read MoreLong Term Beneficiaries of WannaCry
The current worldwide attack from WannaCry is going to have a lasting impact on information security. The question is: what will that be and who will benefit? In this blog post, I will take a contrarian viewpoint and suggest that it will not be beneficial to security practitioners or security businesses. I think business leaders,…
Read MoreRISK: A NEW MOVIE ABOUT JULIAN ASSANGE
Last night I went to a screening of Laura Poitras’s movie about Julian Assange. If you are interested in national security, I highly recommend the film. I had expected a big crowd, but Nashville’s Belcourt was only about 20% full. Love WikiLeaks or hate WikiLeaks, it is likely Assange will continue to be in the…
Read MoreTRADE SECRET THEFT CONTINUES UNABATED
One of the biggest cyber threats that many US companies face is the theft of their intellectual property (IP). This includes trade secrets, patents, software, and copies of tangible goods. The recently released “Update to the IP Commission Report” gives tangible, current information on all four categories. The original report was published in 2013 amidst…
Read MoreTENNESSEE LEGISLATORS MUDDY WATERS AROUND PRIVACY BREACH NOTIFICATION REQUIREMENTS
The Tennessee legislature recently passed a modification to the state privacy breach notification requirements, § 47-18-2107. The modification has been sent to the governor for signature. Unfortunately, the modification just confuses the law’s requirements. The existing code says that a breach notification is required if “unauthorized acquisition of unencrypted computerized data” takes place. The breach…
Read MoreLEADERSHIP CHECKLIST FOR SECURITY PROFESSIONALS
If you are like me, you have read through many articles and books on leadership. Most security professionals come with a technical background that does not directly facilitate leading people. But solutions aren’t easy to find, either. Many leadership training programs seem vague to me. What about “soft skills” vs. “hard skills”, Aristotle vs. Socrates,…
Read MoreSIEM VENDORS HAVE IT ALL BACKWARDS
On my way into the office this morning, I listened to a podcast interview of a well-known SIEM vendor. I got more and more frustrated at the wheel, but did make it to the office without incident. The focus of this conversation was the plethora of log sources that this vendor could ingest—system, network, endpoint—and…
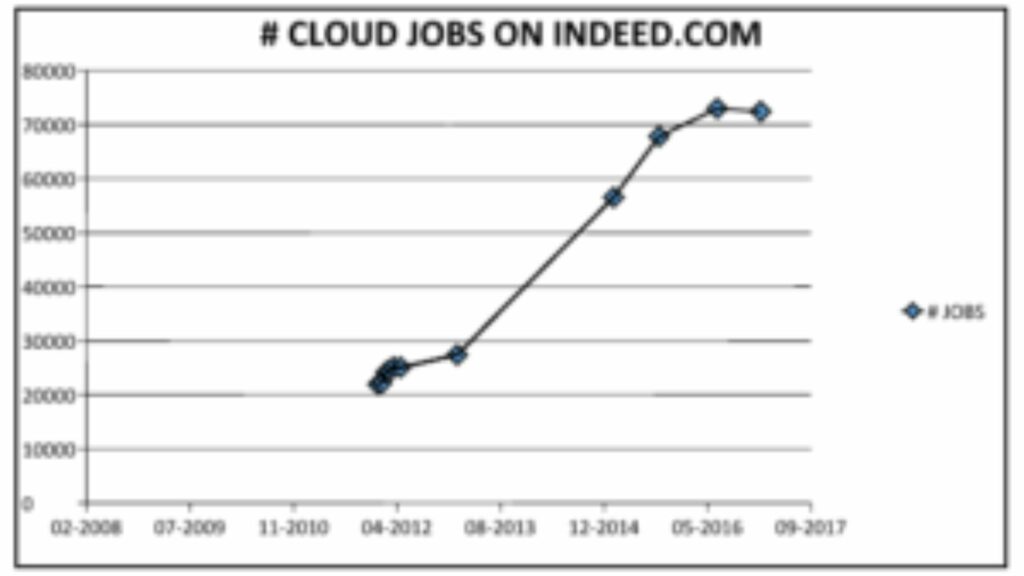
Read MoreCLOUD JOBS PEAKING?
I have been tracking the number of “cloud” jobs listed in Indeed.com for the past five years. See the chart below. This isn’t a scientific survey, but an indication of the openings with the term “cloud” in the job description. Since 2012, this number has gone up continuously. This month’s number shows flattening when compared with…
Read More