Enterprise Cybersecurity Risk Management
“Where security gets down to business” ™

Request Fred Scholl as a Speaker
What are we trying to do?
Our approach to cyber risk management is to start with the business risks, not technology. Only then can we assist you in planning effective risk management approaches. We use techniques including Obashi and TBM (Technology Business Management) to define and document:
- Your business practices and operating models
- Your people and technology resources
- Solutions you build and maintain
- Business outcomes and customers served
What can go wrong?
We use a threat modeling approach to identify cybersecurity risks to the assets highlighted in Step #1. Threat modeling can be done at an enterprise level or specific product or application level. Customized AI based threat analysis combined with input from your organization results in an actionable, prioritized risk register.
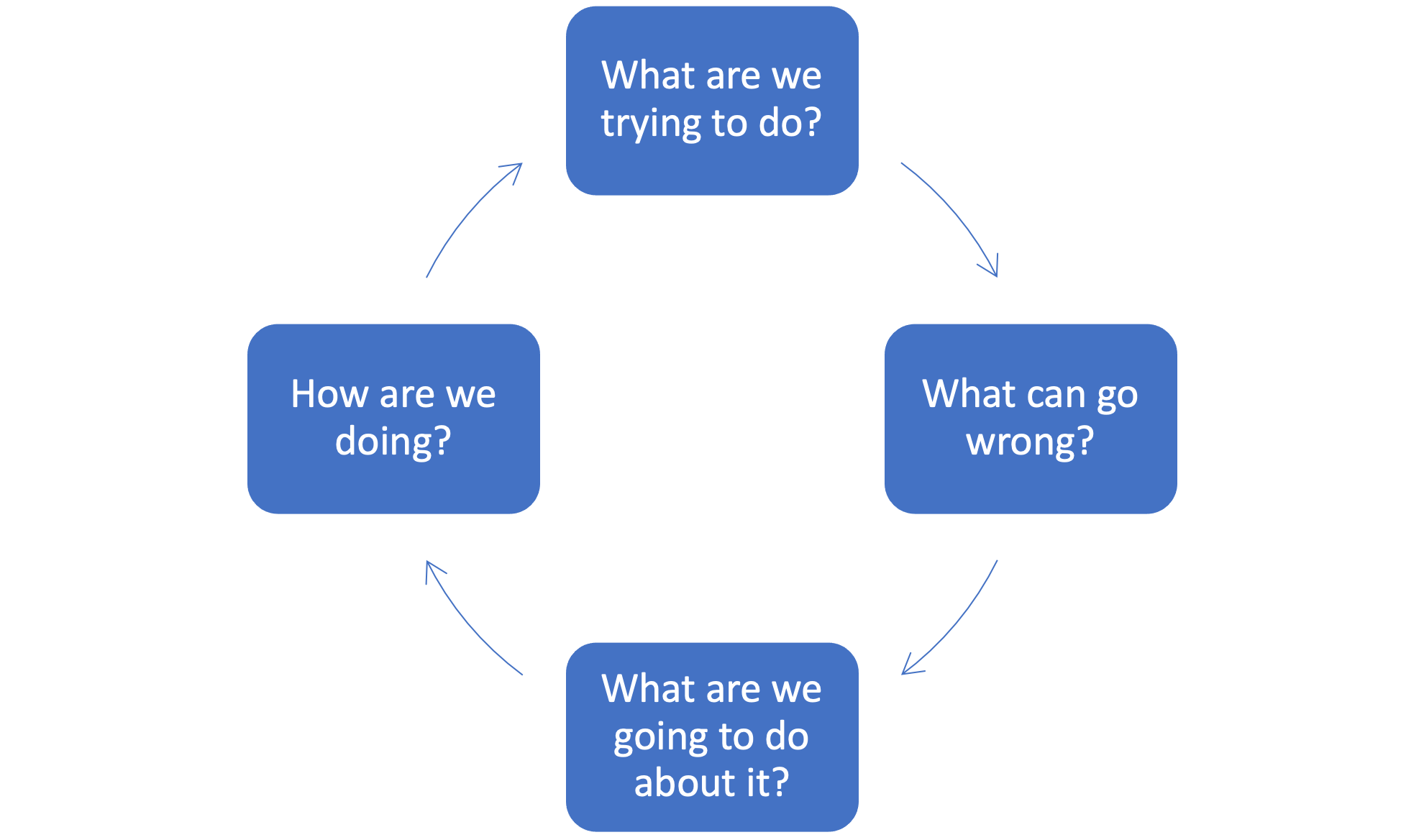
What are we going to do about it?
This step starts with a risk based prioritization of mitigation options. Good cybersecurity is an emergent property of your enterprise system, not a function of technology alone. We call our approach to cybersecurity “People-Centric”. Verizon’s most recent DBIR attributed 82% of breaches to humans. Gartner concurred in its Predicts 2023: “Humans Are the Chief Cause of Security Incidents”.
Our approach to mitigate any of the gaps identified in Step #2 includes:
- Use design thinking approach to improve control effectiveness and efficiency where needed
- Provide education to empower business and IT teams
- Build out an effective three lines of cybersecurity defense
- Align with NIST CSF and COBIT 2019 or other frameworks you may employ
How are we doing?
Ultimately the answer to this question has to be presented to the organization’s board or trustees. So we start from that goal, and work backwards to make sure sufficient data is being gathered and analyzed to provide business-ready answers.
More Services
Expert Services
Extensive experience in cybersecurity planning for organizations across the US.
Vendor Market Acceleration
Design and build better products and create more impactful messaging
Articles in Enterprise Cyber Risk Management
Book an Appointment for Cybersecurity Issues
Request an appointment with Dr. Fred Scholl. We will discuss any cybersecurity issues you have.




