Posts by Frederick Scholl
LEADERSHIP CHECKLIST FOR SECURITY PROFESSIONALS
If you are like me, you have read through many articles and books on leadership. Most security professionals come with a technical background that does not directly facilitate leading people. But solutions aren’t easy to find, either. Many leadership training programs seem vague to me. What about “soft skills” vs. “hard skills”, Aristotle vs. Socrates,…
Read MoreSIEM VENDORS HAVE IT ALL BACKWARDS
On my way into the office this morning, I listened to a podcast interview of a well-known SIEM vendor. I got more and more frustrated at the wheel, but did make it to the office without incident. The focus of this conversation was the plethora of log sources that this vendor could ingest—system, network, endpoint—and…
Read MoreTHE SECRET TO GROWING YOUR SECURITY STARTUP
This week is RSA 2017 and I am counting hundreds of vendors exhibiting in San Francisco. This doesn’t count the others still in stealth mode and off the main show floor. They are all looking for the right formula to survive and grow. But what is that formula? In fact security startups aren’t much different…
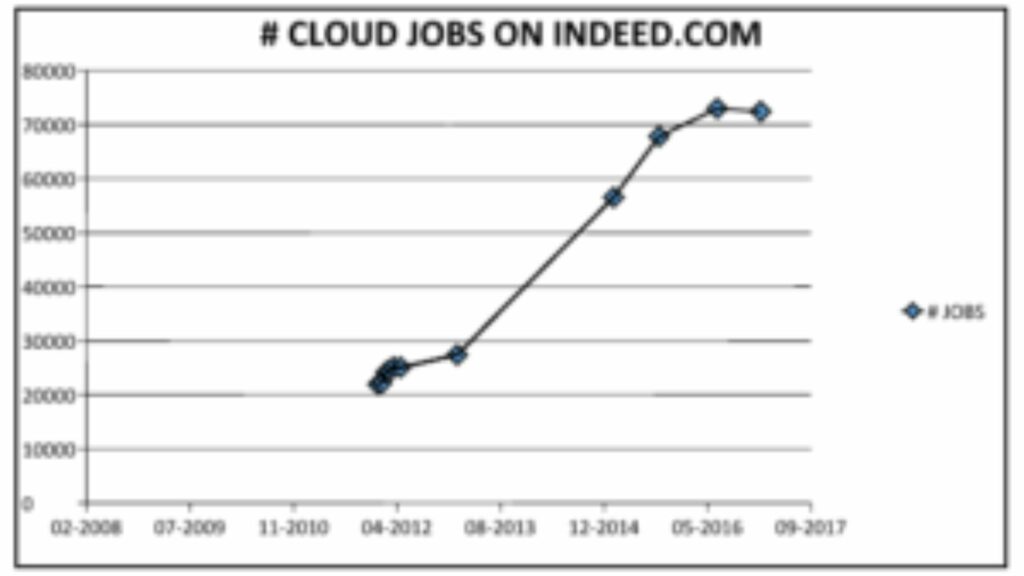
Read MoreCLOUD JOBS PEAKING?
I have been tracking the number of “cloud” jobs listed in Indeed.com for the past five years. See the chart below. This isn’t a scientific survey, but an indication of the openings with the term “cloud” in the job description. Since 2012, this number has gone up continuously. This month’s number shows flattening when compared with…
Read MoreThe Spy Who Couldn’t Spell
Occasionally a book on information security comes along that is required reading by all. The Spy Who Couldn’t Spell is one of those books. Published in 2016 and written by journalist and writer Yudhijit Bhattacharjee, it includes pretty much everything that security professionals deal with every day. The book is non-fiction, dealing with a real-life story of espionage. Here, truth…
Read MoreIS THERE A CYBERSECURITY PROFESSIONALS SHORTAGE?
There is no shortage of headlines stating the cybersecurity professionals shortage as a fact. For example, this one from Information Week. I have taught security at the graduate level, and can report that all my students found good jobs. But I get a little skeptical after reading all of these headlines from other industries: “The worker…
Read MoreNo Blue Pill for Cybersecurity Failures
A few weeks ago, I was asked to comment on the “most underestimated IT security threat”. My answer was “us”. The full post is here. My conclusion is going to be valid for 2017 and at least the next 10-20 years. Why? Because there are no magic pills to prevent cybersecurity failures. Only your own diligence…
Read MorePresidential Cybersecurity Commission Makes Some Good Suggestions
President Obama’s Commission on Enhancing National Cybersecurity issued its report on December 1, and I thought it had some good recommendations. I was expecting a long list of regulatory requirements but did not find those. Now we have to wait to see if the incoming President chooses to follow the recommendations. The report contents were…
Read MoreUnderstanding Intelligence
It is obvious that cybersecurity will continue to play an important part in national security. But as a Washington outsider, it is difficult to see inside government policies and organizations that are responsible for this security. Michael Hayden has taken a significant step in providing this insight through his recent book, Playing to the Edge (2016). …
Read MoreAlign Your Security Program With the Business
Information security used to be part of IT. That has changed recently; security now needs to be independently aligned with the business operations, not just IT operations. The PCI SSC calls this “Business as Usual” (BAU). NIST CSF talks about aligning cybersecurity requirements with business activities. I call this process information security governance and maintain…
Read More